The present and future of IT management is now remote. Whereas pre-pandemic, data centers were populated by teams working side-by-side, now most IT staff work remotely from their homes and other locations. As a result, they’re using secure remote monitoring and management systems to oversee a growing distributed network, including core data centers, colocation facilities, and edge sites.
That trends mirrors what is happening globally. Gartner estimates that by the end of 2021, 51% of all knowledge workers worldwide will be working remotely, up from 27% of knowledge workers in 2019.
While IT teams have gained much-needed work-life flexibility, they are also tackling more responsibilities than ever: strengthening the stability and reliability of digital infrastructures, working with security teams to develop zero-trust architectures, and scaling services to meet soaring business demand. Like other company functions, IT teams are rethinking operations to design for greater resilience, not just efficiency, which can sometimes introduce fragility into processes.
Both Internal and External Groups Have Access to Corporate Networks
As a result, providing IT and security with authorized remote access to networks is more important than ever. However, what IT considers a critical tool to working productively can easily introduce critical gaps into networks if not well-controlled. Excessive access privileges can increase the risk of human error or malicious insider activity. Some 85 percent of data breaches still have a human element. Thus, controlling and right-sizing networking system administrator privileges to exact roles and jobs to be done is an important step to reducing risk.
In addition to system administrators, external parties, such as cloud and managed service providers, colocation teams, and more, have access to corporate networks. A recent survey of IT professionals found that 94 percent give third-party users access to their networks, and 72 percent give them privileged or superuser permissions. As with internal users, IT needs to make sure these privileges are warranted and properly aligned to business requirements and these users’ monitoring and management needs. As a case in point, remember the Amazon contractor who used a firewall vulnerability to execute commands on Capital One’s servers and steal and post data on 106 million customers in the U.S. and Canada. The contractor then executed a command to gain access to privileged credentials and downloaded files stored on AWS. Capital One had to remediate this vast data breach.
5 Steps to Controlling Secure Remote Access for IT and Security
IT administrators can bring greater visibility and control to secure remote access programs by using Vertiv™ Avocent® ADX Ecosystem. This scalable digital platform provides everything IT and security need to monitor and manage their growing device fleet at network locations. Of equal importance, the platform provides multiple layers of security controls to authenticate users and manage their privileges. IT and security teams can use Avocent ADX Ecosystem to:
- Provide secure remote access based on role: The Avocent ADX Ecosystem enables IT to partition internal and external user privileges by role. For example, power management administrators can be granted access to monitor and manage only rack power distribution units (rPDUs) directly, while security can be provided access to just firewalls. In addition, IT can segment access across the same device type, such as servers. An application group could be authorized to access just development and production servers, while the testing group would only have access to testing servers.
- Control what users can see: If users are only authorized to access and manage certain devices, they don’t even need to see other networking devices. This ability to remove devices from users’ views enables Avocent ADX Ecosystem to be used for a variety of purposes. Colocation teams can use elevated privileges to see all devices across all customer accounts, whereas corporate IT teams can only see their own devices at these facilities. Third parties granted enterprise network access can have their views limited to the devices aligned with their duties. Similarly, Avocent ADX Ecosystem can streamline IT management within global companies that operate multiple businesses or divisions. IT teams managing one internal business’s networks don’t see other networks, simplifying their work and preventing actions that could lead to cascading errors.
- Enable privileges based on capabilities: IT can set up dynamic user groups and assign privileges easily using Avocent ADX Ecosystem. Alternatively, IT can use third-party authentication services such as TACACS+ or Active Directory to align appliance roles and authorizations to those set at the corporate level.
Beyond roles, IT can provide users with ultra-granular device privileges. For example, a user may be granted access to run devices and check their status, but not configure them. These privileges obviously must be updated when contractors complete their assignments or users change jobs, get promoted, or leave the company. Segmenting these duties reduces the opportunity for authorized users to perform unapproved actions on devices they use routinely.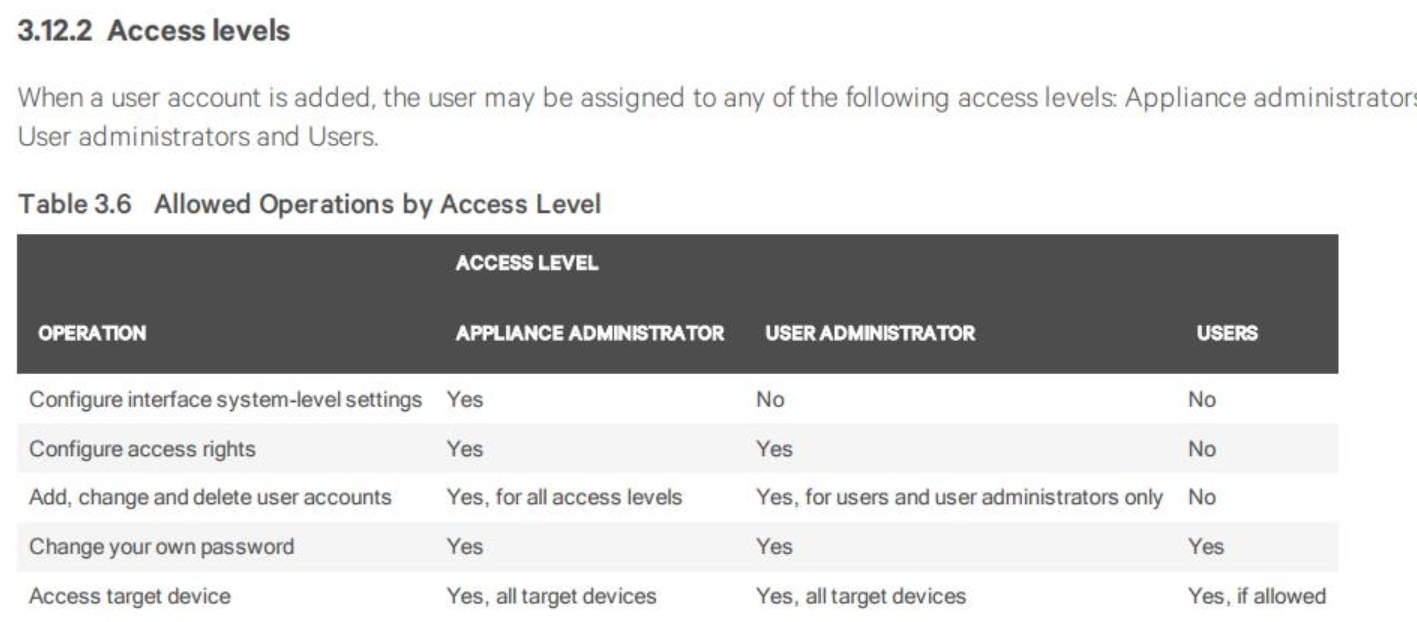
- Control which sessions can be launched on devices: Avocent ADX Ecosystem controls both serial console and keyboard, video and mouse (KVM) sessions. IT administrators can authorize (or decline) user serial sessions to perform routine work. IT administrators can use Vertiv Avocent ACS 8000 Serial Console for both in-band and out-of-band management. The serial console enables users to perform repetitive, non-visual tasks, such as monitoring devices, gathering data, and automating configuration tasks. With Vertiv™ Avocent® ADX IPUHD 4K KVM devices, IT users can use high resolution imagery to guide focused work, such as development and testing, obtaining visual feedback on their activities.
- Track all user activity: IT can use Avocent ADX Ecosystem to audit all user activity, quickly zeroing in on any issues. IT can monitor every keystroke that users make when accessing devices with the Avocent ACS 8000, the timeline for all actions, and activity across devices. IT can also set up alerts on strings, so that if users take an action, such as typing a code or sending a text or email, administrators are alerted.
Sometimes issues occur when multiple users perform actions on a device, and unintended consequences ensue. By being able to track and interpret these actions in context, IT can do faster troubleshooting, as well as keep and provide records for compliance purposes.
Conclusion
As digital pressures grow, IT needs to strike a balance between providing secure remote access to networking devices – and tightly controlling these privileges. Vertiv™ Avocent® ADX Ecosystem provides IT administrators with all the tools they need to grant, revoke, control, and monitor granular access privileges. As a result, Avocent ADX Ecosystem can be a powerful tool in IT’s drive to work with other teams and third parties to accelerate business growth.




